Zero-day vulnerability
|
Read other articles:

Bobo adalah serial komik Prancis-Belgia yang dibuat oleh Paul Deliège dan Maurice Rosy. Serial ini menampilkan seorang tahanan eponymous dari penjara Inzepocket (di saku dengan aksen Prancis). Dalam bahasa Belanda, nama serial tersebut adalah Jaap. Sejarah Bobo pertama kali muncul dalam mini-récit (cerita mini) di majalah Spirou pada 11 Mei 1961.[1] Pada tahun-tahun awal, ditulis oleh Rosy, yang juga mengambil tanggung jawab artistik selama periode singkat di tahun 1970-an.[2 ...
Pour les articles homonymes, voir Occident (homonymie). Pour l’article ayant un titre homophone, voir Oxydant. Si ce bandeau n'est plus pertinent, retirez-le. Cliquez ici pour en savoir plus. Cet article ne cite pas suffisamment ses sources (juin 2022). Si vous disposez d'ouvrages ou d'articles de référence ou si vous connaissez des sites web de qualité traitant du thème abordé ici, merci de compléter l'article en donnant les références utiles à sa vérifiabilité et en les liant ...

Si ce bandeau n'est plus pertinent, retirez-le. Cliquez ici pour en savoir plus. Cet article peut avoir été modifié (voire créé) en échange d'une rémunération ou d’avantages non déclarés, ce qui constitue le cas échéant une violation des conditions d'utilisation de Wikipédia (décembre 2022). L'article doit être relu — et modifié si nécessaire — par des contributeurs indépendants pour apporter un regard critique aux contributions effectuées en violation des conditions ...

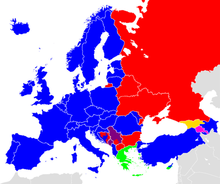
2022 Wisconsin Attorney General election ← 2018 November 8, 2022 2026 → Nominee Josh Kaul Eric Toney Party Democratic Republican Popular vote 1,333,369 1,298,369 Percentage 50.6% 49.3% County results Congressional District results State Senate District results State Assembly District results Precinct resultsKaul: 40–50% 50–60% 60–70% ...

Moussa Sissoko Moussa Sissoko pada tahun 2012Informasi pribadiNama lengkap Moussa SissokoTanggal lahir 16 Agustus 1989 (umur 34)Tempat lahir Le Blanc-Mesnil, PrancisTinggi 1,87 m (6 ft 2 in)Posisi bermain GelandangInformasi klubKlub saat ini FC NantesNomor 17Karier junior1995–1999 Espérance Aulnay1999–2001 Red Star FC2001–2003 Espérance Aulnay2003–2007 ToulouseKarier senior*Tahun Tim Tampil (Gol)2007–2013 Toulouse 192 (20)2013–2016 Newcastle United 118 (11)2...

komunitas Wikimedia beralih ke halaman ini, yang bukan mengenai Komunitas Wikipedia. Wikimedia beralih ke halaman ini, yang bukan mengenai MediaWiki atau Yayasan Wikimedia. Wikimedia movementFoto grup Wikimania 2023FokusBebas, konten terbuka, proyek-proyek Internet berbasis wikiWilayah layanan WorldwideJasaMenulis dan menyunting Wikipedia, Wiktionary, Wikimedia Commons, Wikidata, Wikiquote, Wikibooks, Wikisource, Wikispecies, Wikinews, Wikiversity, dan WikivoyagePerangkat lunak pengembang Med...
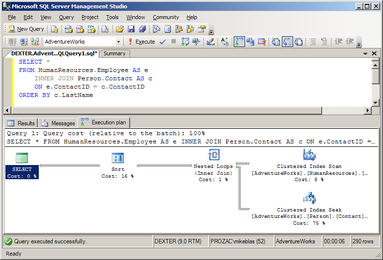
A query plan (or query execution plan) is a sequence of steps used to access data in a SQL relational database management system. This is a specific case of the relational model concept of access plans. Since SQL is declarative, there are typically many alternative ways to execute a given query, with widely varying performance. When a query is submitted to the database, the query optimizer evaluates some of the different, correct possible plans for executing the query and returns what it cons...

NASCAR team This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed.Find sources: Sam Hunt Racing – news · newspapers · books · scholar · JSTOR (January 2020) (Learn how and when to remove this message) Sam Hunt RacingOwner(s)Sam HuntPrincipal(s)Allen Hart (Technical dir.)BaseMooresville, North CarolinaSeriesNASCAR Xfinity Series...

この記事は検証可能な参考文献や出典が全く示されていないか、不十分です。出典を追加して記事の信頼性向上にご協力ください。(このテンプレートの使い方)出典検索?: コルク – ニュース · 書籍 · スカラー · CiNii · J-STAGE · NDL · dlib.jp · ジャパンサーチ · TWL(2017年4月) コルクを打ち抜いて作った瓶の栓 コルク(木栓、�...

Mexican composer (1882–1948) For the Mexican boxer, see Manuel Ponce (boxer). This article includes a list of general references, but it lacks sufficient corresponding inline citations. Please help to improve this article by introducing more precise citations. (May 2009) (Learn how and when to remove this message) Manuel Ponce Manuel María Ponce Cuéllar (8 December 1882 – 24 April 1948), known in Mexico as Manuel M. Ponce, was a Mexican composer active in the 20th century. His work as a...

Questa voce sull'argomento cestisti portoricani è solo un abbozzo. Contribuisci a migliorarla secondo le convenzioni di Wikipedia. Segui i suggerimenti del progetto di riferimento. Deán Borges Nazionalità Stati Uniti Porto Rico Altezza 196 cm Peso 100 kg Pallacanestro Ruolo Ala piccola Termine carriera 2006 CarrieraGiovanili 1986-1991 Wagner SeahawksSquadre di club 1986-1987 Marat. de Coamo561989-1995 Marat. de Coamo2131996-1997 Avan. de Villalba631998&...

本條目存在以下問題,請協助改善本條目或在討論頁針對議題發表看法。 此條目需要編修,以確保文法、用詞、语气、格式、標點等使用恰当。 (2013年8月6日)請按照校對指引,幫助编辑這個條目。(幫助、討論) 此條目剧情、虛構用語或人物介紹过长过细,需清理无关故事主轴的细节、用語和角色介紹。 (2020年10月6日)劇情、用語和人物介紹都只是用於了解故事主軸,輔助�...

Variations of the economic philosophy This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed.Find sources: Types of socialism – news · newspapers · books · scholar · JSTOR (February 2023) (Learn how and when to remove this message) Part of a series onSocialism HistoryOutline Development Age of the Enlightenment French Revolution...

The ActGenre Kasus nyata Drama Antologi Pembuat Nick Antosca Michelle Dean Pemeran Patricia Arquette Joey King AnnaSophia Robb Chloë Sevigny Calum Worthy Penata musikJeff RussoNegara asalAmerika SerikatBahasa asliInggrisJmlh. musim1Jmlh. episode8 (daftar episode)ProduksiProduser eksekutif Nick Antosca Michelle Dean Britton Rizzio Gregory Shephard ProduserJan Peter MeyboomDurasi48–60 menitRumah produksi Eat the Cat Writ Large Universal Content Productions Rilis asliJaringanHuluRilis2...

El Ayuntamiento de México fue la entidad legislativa y administrativa de la ciudad de México creado en 1521 durante el gobierno español hasta el año de 1929 en el México Independiente cuando fue suprimido su ayuntamiento. En el México independiente fue solo el órgano administrativo de la Municipalidad de México, que abarcó territorialmente a la Ciudad de México y a las villas de Guadalupe Hidalgo, Tacubaya y Azcapotzalco; esta municipalidad fue desaparecida en 1970, cuando su territ...

Israeli Druze officer of the IDF Ghassan AlianNative nameרסאן עליאןBorn (1972-03-21) 21 March 1972 (age 52)Shefa-'Amr, IsraelAllegiance IsraelService/branch Israel Defense ForcesYears of service1990–Rank Aluf (Major General)UnitCoordinator of Government Activities in the TerritoriesBattles/wars First Intifada South Lebanon conflict (1985–2000) 2006 Lebanon War Operation Cast Lead Operation Pillar of Defense Operation Protective Edge Israel–Hamas war Ghassan Alian...

一个小型的逐帧动画,显示了硬币的移动过程 Mary and Gretel (1916) 定格動畫 (英語:Stop motion animation),又名停格動畫、逐格動畫、逐帧动画,是一种动画技术,其原理即将每帧不同的图像连续播放,从而产生动画效果。最基本製作定格動畫的方法是利用相機作拍攝工具,為主要對象拍攝一連串的相片,每張相片之間為拍攝對象作小量移動,最後把整輯相片快速地連續播放便完�...

Questa voce sull'argomento società calcistiche inglesi è solo un abbozzo. Contribuisci a migliorarla secondo le convenzioni di Wikipedia. Gillingham F.C.Calcio The Gills Segni distintiviUniformi di gara Casa Trasferta Colori sociali Blu, bianco SimboliStallone Dati societariCittàGillingham Nazione Inghilterra ConfederazioneUEFA Federazione FA CampionatoFootball League Two Fondazione1893 Presidente Paul Scally Allenatore Neil Harris StadioPriestfield Stadium(11.582 posti) Sito we...
Pour les articles homonymes, voir Graupner. Christoph Graupner Partition autographe de la cantate Wir haben nicht mit Fleisch und Blut zu kämpfen Données clés Nom de naissance Christoph Graupner Naissance 13 janvier 1683 Kirchberg, Électorat de Saxe Décès 10 mai 1760 (à 77 ans) Darmstadt, Landgraviat de Hesse-Darmstadt Activité principale Compositeur, claveciniste modifier Paraphe de Christoph Graupner. Christoph Graupner, né le 13 janvier 1683 à Kirchberg, mort le 10 mai 1760...

Cet article est une ébauche concernant une localité bulgare. Vous pouvez partager vos connaissances en l’améliorant (comment ?) selon les recommandations des projets correspondants. Pour les articles homonymes, voir Montana (homonymie). Montana Монтана Héraldique Administration Pays Bulgarie Oblast Montana Maire Zlatko Jivkov (Indépendant) Code postal 3400 Démographie Population 39 595 hab. (en 2017) Géographie Coordonnées 43° 25′ 00″ nord,...

